Solutions
Securing your business doesn't have to be complicated. Our EDR, SIEM, and ITDR solutions are designed to be accessible and effective, providing a unified view of your security posture and protecting you from modern cyber threats.
EDR
Endpoint Detection and Response (EDR) is a technology that continuously monitors and records activity on endpoints, such as laptops, servers, and mobile devices. It goes beyond traditional antivirus by providing a detailed view of all events, enabling our security team to detect and investigate suspicious behavior.
The primary goal of EDR is to prevent, detect, and respond to advanced cyber threats that bypass conventional security defenses.

Deploys in minutes
Our solution uses a lightweight agent that deploys in minutes, not hours or days. This means you get immediate protection and don't have to deal with complex, time-consuming installations.
Automated Threat Containment
Our EDR takes immediate, decisive action. The moment a threat is detected, we have the ability to instantly isolate the affected endpoint, neutralising the attack before it can spread.
Detailed Reports
Our detailed reports transform raw data into strategic intelligence. Get a complete picture of every security incident enabling you to understand the full scope of an attack and make informed decisions to strengthen your defense.
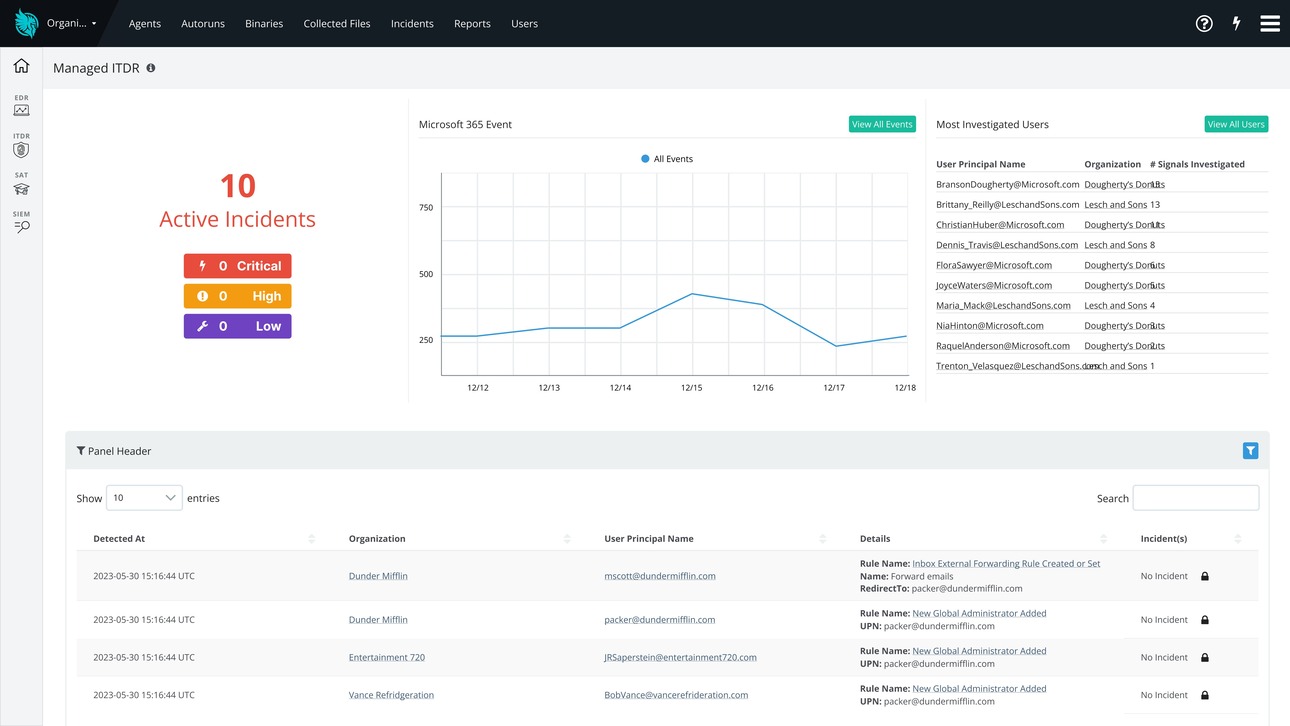
ITDR
Identity Threat Detection and Response (ITDR) is a security solution focused on protecting user identities. It continuously monitors and analyses user and account activity for suspicious behavior, such as impossible travel, unusual login times, or credential abuse.
By moving beyond traditional identity management, ITDR detects threats that exploit compromised accounts and automatically responds in real-time to neutralise them, preventing attackers from gaining a foothold and moving laterally across the network.
Secures Every Identity
In the modern threat landscape, identity is the new perimeter. Our ITDR solution provides continuous, 24/7 protection for every user account, whether on-premises or in the cloud.
We monitor every point of access, ensuring all identities are fortified against compromise.
Monitors for Anomalous Behavior
Our platform moves beyond simple authentication checks, leveraging advanced intelligence to monitor for anomalous behavior.
We detect unusual login locations, impossible travel patterns, and other suspicious activities that signal a potential breach, catching sophisticated attacks that bypass traditional security measures.
Automated Account Isolation
When a threat is detected, we don't just alert you, we act. Our ITDR solution automatically isolates compromised accounts and revokes access in real-time, instantly shutting down an attacker's foothold and preventing any lateral movement.
This proactive containment neutralises threats before they can escalate.
SIEM
Security Information and Event Management (SIEM) is the central command of our security operations. It ingests and normalises security logs from every corner of your network, from firewalls and endpoints to applications and identity systems.
Our SIEM uses advanced analytics to correlate this data, finding hidden threats and patterns of attack that would be invisible to individual security tools. This gives you a unified, real-time view of your entire security posture, allowing for faster detection and more decisive action against threats

Single Pane of Glass
Our SIEM gives you a unified command center for your entire security posture. By aggregating all security data into one intuitive dashboard, we eliminate the noise and complexity of multiple tools.
You get a complete, real-time view of your environment, allowing you to monitor and respond to threats with unprecedented clarity.
Advanced Threat Correlation
We don't just collect data; we make sense of it. Our platform uses powerful analytics to correlate seemingly unrelated security events from across your network.
This is how we connect the dots and reveal hidden attack patterns, detecting sophisticated threats that would be invisible to individual security tools.
Centralised Log Management
Every security event is a piece of the puzzle. Our SIEM centralises and normalises all of your security logs into a single solution.
This not only streamlines compliance and simplifies forensics, but it also ensures that all data is ready for instant analysis, allowing us to investigate incidents faster and more effectively.
